Security Requirements of Internet Voting
The foundations of democratic societies are elections. Due to their central importance to society, elections are bound to high legal requirements, which are usually specified as election principles in national constitutions. To date, technological advance has reached elections and Internet voting is a buzzword in the field of information technology. Many Internet voting systems have been proposed in research and some have even been used in legally binding elections. In spite of their individual strengths and benefits, those systems cannot enforce legal requirements to their full extent. This stems from the fact that legal requirements partially oppose each other. To evaluate Internet voting systems with regard to their legal compliance, it is therefore of fundamental importance to have technical requirements against which Internet voting systems can be evaluated.
The first goal of this research was to determine technical requirements for Internet voting systems on the basis of legal requirements. The second goal of our work was to separate security requirements from non-security requirements. Based on the determined security requirements, the third goal of this research was to establish a foundation for the security evaluation of Internet voting systems.
Research Method
Based on the interdisciplinary method KORA and preliminary work of ModIWa 1 we derived technical requirements for Internet voting systems on the basis of election principles declared in the German Constitution and further constitutional rights, namely the Informational Self-determination and the Secrecy of Telecommunications.
The legal criterion assurance derived within ModIWa 1 is an instrumental criterion, which ensures the enforcement of all other criteria even in the presence of attacks and failures. On the basis of the assurance criterion, we classified technical requirements into security and non-security requirements.
To evaluate to which extent Internet voting systems satisfy security requirements, we proposed a uniform set of adversarial capabilities. These capabilities serve analysts and decision makers to the same extent, as they form a common specification language for assurance guarantees (analysts) and objectives (decision maker).
Technical Requirements for Internet Voting Systems
An overview of the determined technical requirements and their relation to legal criteria is provided in Figure 1. The technical requirements are outlined in the following:
- System Usability: The voting system is usable to all eligible voters.
- Vote Integrity: The voting system ensures that each vote is correctly included in the election result.
- System Accessibility: The voting system is accessible to all eligible voters.
- Voter Availability: The voting system does not exclude eligible voters from casting their intention.
- System Availability: The voting system is available to all eligible voters during the entire voting phase.
- System Reachibility: The voting system is physically accessible to all eligible voters.
- Eligibility: The voting system ensures that only eligible voters' votes are included once in the election result.
- System Neutrality: The voting system does not influence the eligible voter's intention.
- Fairness: The voting system does not provide evidence about any eligible voter's intention before the end of the election.
- Vote Secrecy: The voting system does not provide more evidence about a specific eligible voter's intention than the election result does.
- Individual Verifiability: The voting system offers each eligible voter the possibility to verify that her intention has been correctly included in the election result.
- Public Controllability: The voting system offers any observer the possibility to control that all technical requirements resulting from the principles universal, direct, equal, free, and secret elections are enforced.
- Data Minimization: The voting system shall only request and store the personal data without which the system does not operate correctly.
- Data Inspection: The voting system shall offer the voter a possibility to view the personal data about herself stored and processed by the system.
- Data Access Protection: The voting system shall prevent unauthorized parties from viewing voter data.
- Data Adaptation: The voting system shall offer the voter the possibility to adapt her personal data.
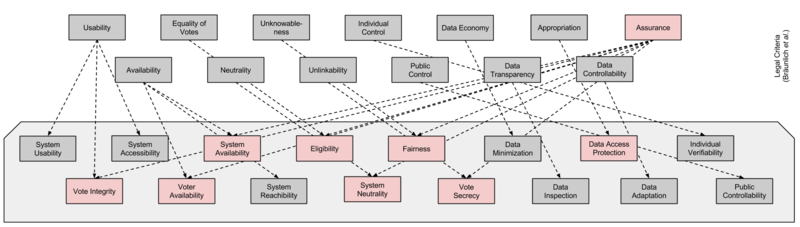
Figure 1: Technical requirements for Internet voting systems derived from legal criteria determined by Bräunlich et al. (2013).
Security Requirements for Internet Voting Systems
The legal criterion assurance (see the red box on the third layer in Figure 1) is an instrumental criterion, which ensures the enforcement of all other criteria even in the presence of attacks and failures.
From the assurance criterion several technical requirements were identified as security requirements, i.e. requirements that have to be maintained even in the presence of adversaries. These requirements are highlighted by red boxes.
Adversarial Capabilities
As composition of previous research results, we classified adversarial capabilities into three sub-classes, namely corruption capabilities, channel capabilities, and computational capabilities. Note that in the following paragraphs, variables are indicated by [*X*].
The security of Internet voting might be threatened by corrupt service providers carrying the election duties, be it either in terms of administrators, hardware, or software components. We distinguish between service providers that operate in an offline environment, i.e. service providers that are not in direct contact with voters, and those that operate in an online environment, i.e. service providers that are in direct contact with voters.
- The adversary can corrupt a [*offline service provider*].
- The adversary can corrupt a [*online service provider*].
On the voter-side, another crucial component is the device used to cast a vote. This device might be under adversarial control.
- The adversary can corrupt a [*voting device*].
The security of the voting systems does, however, not only depend on the trustworthiness of certain service providers or devices. Rather, these systems’ security relies on the human-computer interaction. Voters might be interested in or coerced into deviating from their original voting intention. We distinguish between the capabilities that the adversary might receive objects or data from voters (voter output), e.g. vote receipts, and that the adversary might provide voters with objects or data (voter input), e.g. instructions to cast a vote in a unique and identifiable manner.
- The adversary can receive objects/data from a [*voter*].
- The adversary can send objects/data from a [*voter*].
We define one capability which indicates whether the adversary is capable of controlling the communication between voting devices and service providers or the communication between service providers.
- The adversary can control a [*communication channel*] between a voting device and a service provider or between two service providers.
We define one adversarial capability indicating that the channel between a voter and her device(s) might be controlled by the adversary.
- The adversary can control a [*communication channel*] between a voter and her voting device(s).
A number or scientific works consider adversaries capable of obtaining (practically) unlimited computational resources. This is captured by the following capability.
- The adversary is computationally unrestricted.
Publications
Analysis of Security and Cryptographic Approaches to Provide Secret and Verifiable Electronic Voting: Neumann, S.; Budurushi, J.; Volkamer, M. 2014. Design, Development, and Use of Secure Electronic Voting Systems. Ed.: D. Zissis, 27–61, IGI Global, Hershey (PA). doi:10.4018/978-1-4666-5820-2.ch002
Evaluation and Improvement of Internet Voting Schemes Based on Legally-Founded Security Requirements: Neumann, S. Dissertation. 2016. Darmstadt
