TORPEDO - Add-on to support users in detecting phishing e-mails

Phishing is a method fraudsters use to defraud or harm you.They send you phishing e-mails, i.e. messages containing malicious links. Thus, in order to effectively detect phishing emails, it is necessary to carefully check the web address (also called URL) behind the link. TORPEDO (TOoltip-poweRed Phishing Email DetectiOn) helps to expose malicious links in phishing e-mails so that you can expose their attempts to deceive you. It exists as an add-on for browsers (Chrome, Firefox) as well as for the Thunderbird e-mail client.
Functionality
TORPEDO displays the relevant information for the check directly next to the link in a tooltip(-overlay), so that it is easier to perform the check with TORPEDO. In addition, TORPEDO distinguishes different risk levels of links and thus shows you when it is important to check the web address behind the link before clicking the link. The following risk levels are shown:
Green - the risk of clicking the link is rated as low. The reason is that the domain is part of a list of most visited websites of all internet users in Germany.
In the following example “Click here” is the link.
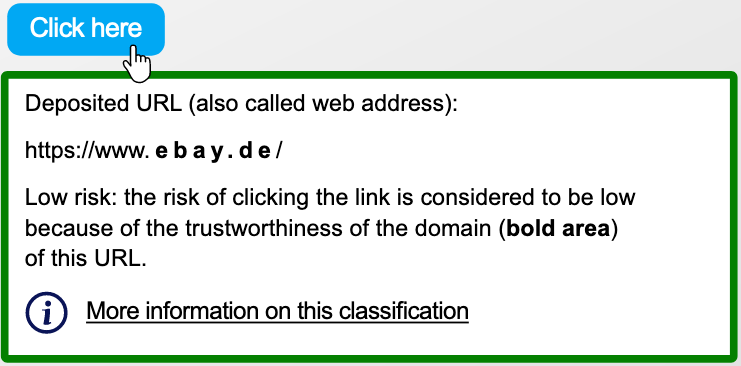
Blue - the risk of clicking the link is rated as low. The reason is that you either already clicked the domain twice or manually added it to the list of trusted domains.
In the following example https://www.paypal.com/de/home is the link.
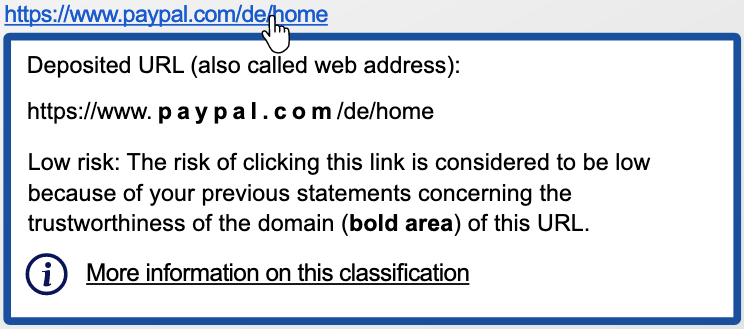
Grey - the risk of clicking the link is rated as unknown. In these cases, you must check the domain yourself to find out whether the link will lead to a phish-attack or not. To avoid rash clicking, the link is deactivated for three seconds.
The following section contains one phishing and one legitimate example.
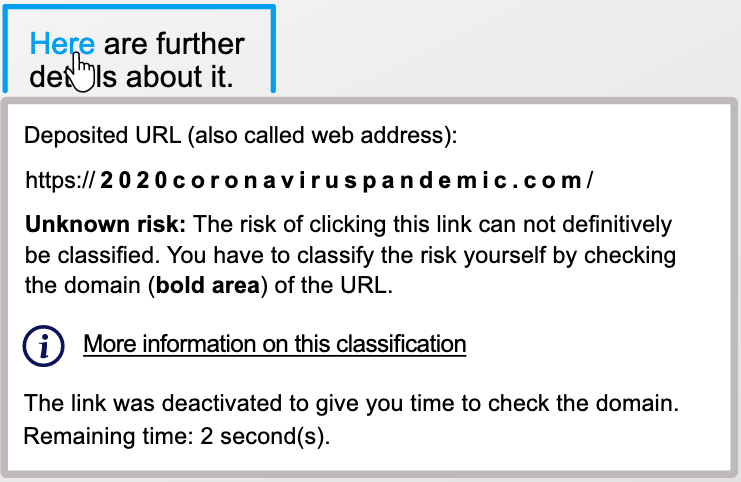
Example 1: Imagine you open an email. The design of the email and the sender make it look like clicking the link will open a New York Times website on the subject "Covid-19".
In this example “Here” is the phishing link since you are not forwarded to the New York Times website.
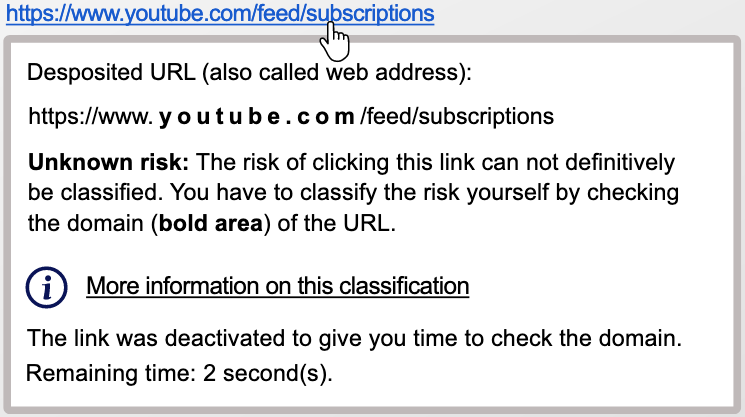
Example 2: Imagine you open an email. The design and the sender suggest that clicking the link would lead to a website of YouTube.
In this case https://www.youtube.com/feed/subscriptions is the legitimate link because the domain belongs to YouTube.
Grey with warning symbol - the risk of clicking this link is rated as unknown. The warning symbol is displayed since at least one indicator that is often used in phishing attacks was found. However, it does not necessarily mean that it is a phishing URL. Legitimate emails may contain these indicators as well. You must check yourself whether the link leads to a website that might perform a phishing attack or not. As in case 3 clicking is deactivated for 3 seconds to avoid rash clicking of the link.
The following examples will show one phishing and one legitimate link with a warning symbol due to an identified indicator. The indicators are that the link text does not match the domain of the link.
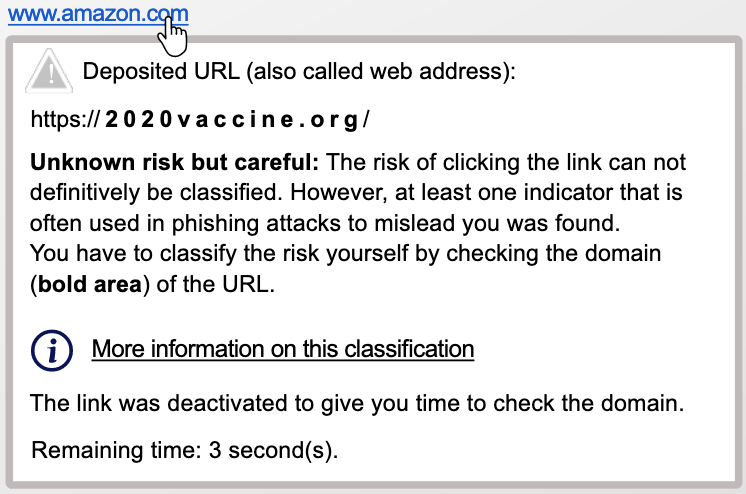
Example 1: Imagine you open an email. The email looks like it came from amazon and contains links to the website of amazon.
In this example www.amazon.com is the phishing link. The dialogue shows that the link does not lead to the domain amazon.com. The warning symbol appears because the domain of the link text does not match the domain of the legitimate deposited link.
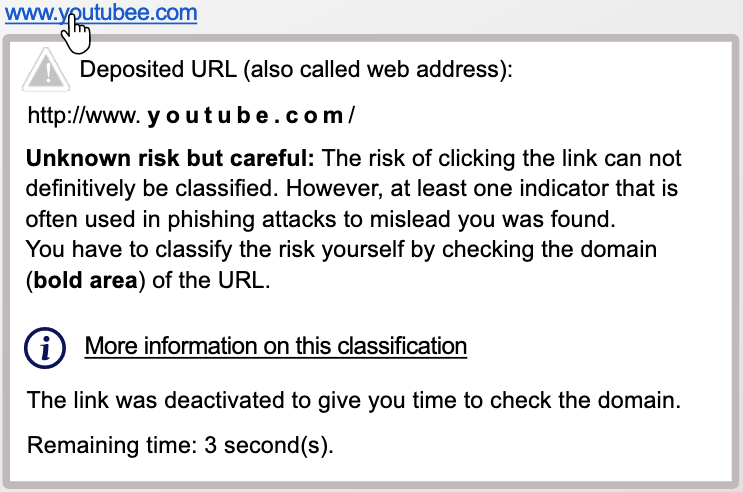
Example 2: Imagine you open an email. The design and the sender suggest that clicking the link would lead to a website of YouTube.
In this example www.youtubee.com is a legitimate link. The warning symbol is displayed since the link text does not match the domain of the deposited link: the link text contains a typo. YouTube is spelled with two “e” instead of just one. Typos happen in emails. Since the domain of the deposited link is from YouTube this is not a phishing attack.
Special cases – TORPEDO supports several special cases, such as short URLs and redirects. To ensure that these are configured according to your needs, we recommend that you take a look at the settings. The settings can be opened by right clicking on the tooltip.
check out the settings for more options
Settings
In the settings there are 4 different options:
- "Timer" lets you change the settings of the timer, e.g. you can increase or decrease the time or deactivate the timer completely. You can also activate and deactivate the different modes. If the privacy mode is activated, links are always opened via the resolved domain and not via the origin link. Also, short URLs are not resolved directly, but only after your confirmation. If Security Mode is enabled, you will see the gray case with a warning icon only after the second referrer. Otherwise, this already happens with the first one.
- "Domains" lets you deactivate the list of most visited websites for the green case. You can also add your own cases to the Blue case list here.
- "Referrer" lets you view the currently integrated referrers and add your own.
- "Short URL" lets you view the currently integrated short URLs and add your own.
Download
- Browser: You can download TORPEDO for Firefox here.
- Thunderbird: You can download TORPEDO directly in Thunderbird.
- If you are interested in the source codes of the add-ons, you can find them at GitHub (Thunderbird, Firefox).
Publications
- Better Together: The Interplay Between a Phishing Awareness Video and a Link-centric Phishing Support Tool
Berens, B.; Schaub, F., Mossano, M.; Volkamer, M.
2024, Mai Conference on Human Factors in Computing Systems (CHI 2024), Honolulu, Hawai'i, USA, 11.-16.05 Mai 2024 - User experiences of TORPEDO: TOoltip-powered phishing email DetectiOn: Melanie Volkamer, Karen Renaud, Benjamin Reinheimer, Alexandra Kunz. In: Computers & Security, February 2017
- TORPEDO: TOoltip-poweRed Phishing Email DetectiOn: Melanie Volkamer, Karen Renaud und Benjamin Reinheimer. In: 31st International Conference on ICT Systems Security and Privacy Protection - IFIP SEC 2016, Juni 2016.
