ACCESS - Authentication ChoiCE Support System
Authentication can be performed in a variety of ways, such as entering knowledge-based information (e.g., PIN or password), using a token (e.g., smart card or usb-dongle), or based on biometric features (e.g., fingerprint). Knowledge-based schemes are most commonly used (text password). Token-based systems are e.g. used in access control for buildings (e.g. key cards in hotels or transponders). Biometric systems are nowadays successfully used in the mobile sector (e.g. fingerprint readers in smartphones).
The authentication methods differ in aspects such as usability, security or deployability and offer different advantages and disadvantages. Passwords can be forgotten, duplicated, or shared. Chip cards suffer from the need to carry them around and for scanning a fingerprint specialized reader is needed. Therefore, the challenge is to choose a suitable authentication scheme for the particular application scenario of the service or website based on its requirements.
What is ACCESS?
ACCESS is a platform that helps developers and decision makers to select appropriate authentication schemes. It allows specifying the requirements needed for an authentication scheme to be suitable. Then, the platform compares the requirements with the entries of its knowledge base and lists the five most suitable authentication schemes and their suitability scores for the corresponding scenario. The platform comprises three modules: the information module, the discussion module, and the decision support module. All modules have been evaluated in user studies.
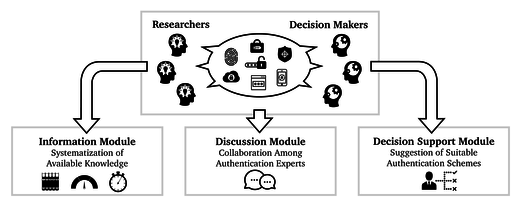
Information Module
Using the information module, users of the platform can access the information about the different authentication systems, features and sub-features held in the platforms knowledge base. Clicking on an authentication scheme gives the user more information about the corresponding authentication scheme and the sub-features that it fulfills.
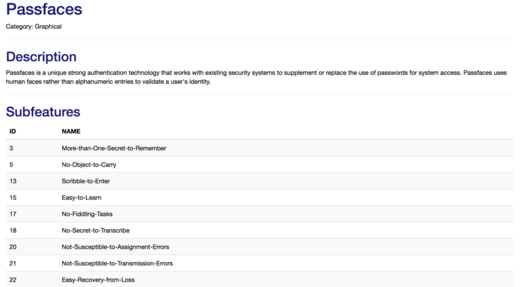
Interface showing the information for the authentication scheme Passfaces (excerpt)
Discussion Module
The discussion module allows users to participate in enhancing the knowledge base. Due to the constant development of many authentication schemes, a user can submit proposed changes such as whether an authentication scheme fulfills a sub-feature or even add completely new authentication schemes. After a reviewing and discussion process with the users, the proposed change is either accepted and stored in the knowledge base or rejected.
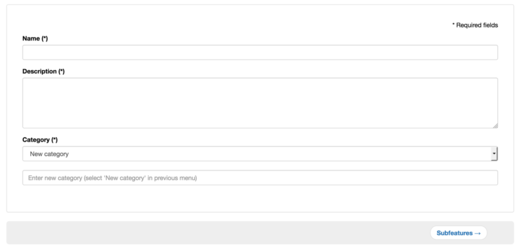
Interface showing the first step of proposing a new authentication scheme for the knowledge base
Decision Support Module
The decision support module combines the knowledge base with the requirements to provide the user with the selection of the most suitable authentication schemes for the user's application scenario. In the first step, the user selects the features which are important to the particular application scenario and sorts them according to their importance. Features from three groups can be selected:
- Deployability
- Usability
- Security
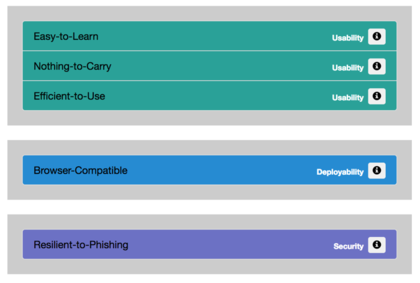
Example for the selection of requirements from the three groups usability, deployability, and security
The second step allows the user to set hard constraints. The number of considered authentication schemes from the knowledge base is updated corresponding to the selected hard constraints. Once the user has made all the settings, he can advance to the results screen which displays the five most suitable results, sorted according to their performance values. In addition, for each of the five proposed authentication systems, the performance results for each selected feature are displayed.
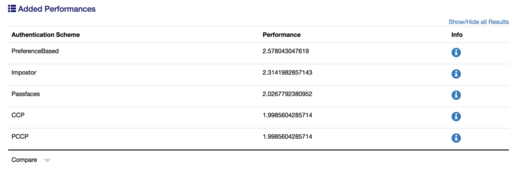
List of the five most suitable authentication schemes
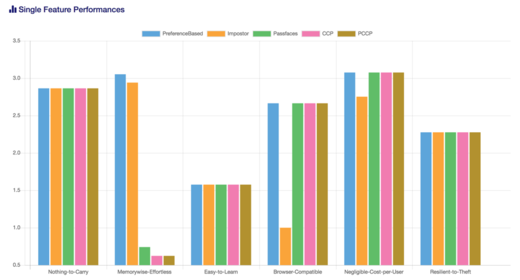
Performance values of the authentication schemes for each of the requirements
Usage & Contact
We provide ACCESS as a service for the public and in particular the research community. The decision support module and the information module can be used without registration. To use the discussion module (editing the data and participating in discussions) a user account is needed. An "invite code" for the registration can be requested from Peter Mayer (peter.mayer(a-t)kit.edu). Should you use ACCESS, please reference our corresponding publications.
ACCESS is open source software. The source code can be viewed on GitHub External Link.
Publications
- Keep on Rating - On the Systematic Rating and Comparison of Authentication Schemes: Zimmermann, V.; Gerber, N.; Kleboth, M.; Preuschen, A. von; Schmidt, K.; Mayer, P. 2019. Information & Computer Security.
- The Quest to Replace Passwords Revisited - Rating Authentication Schemes: Zimmermann, V.; Gerber, N.; Kleboth, M.; Preuschen, A. von; Schmidt, K.; Mayer, P. 2018. Proceedings of the 12th International Symposium on Human Aspects of Information Security and Assurance (HAISA 2018)
- Towards Collaboratively Supporting Decision Makers in Choosing Suitable Authentication Schemes: Mayer, P., Neumann, S. & Volkamer, M., 2016. POSTER. Conference on Computer and Communications Security. pp. 1817–1819.
- Supporting Decision Makers in Choosing Suitable Authentication Schemes: Mayer, P. et al., 2016. International Symposium of Human Aspects of Information Security Assurance. pp. 67–77.
- ACCESS: Describing and Contrasting: Renaud, K., Volkamer, M. & Maguire, J., 2014. Human Aspects of Information Security, Privacy, and Trust. pp. 183–194.
