Guests in 2022
December
Marcus Brinkmann (Ruhr-University Bochum)
Marcus Brinkmann gave an overview on their results regarding email encryption, he presented follow-up results that gives insight into the challenges in mitigating them, and he talked about recent standardisation efforts to address them cryptographically.
Mehrdad Bahrini (University of Bremen)
Medad Bahrini showed how to use HCI interaction approaches, such as gamification, personal data visualisation and user right transparency to empower users to protect their data in the smart devices sphere.
November
Lukas Struppek (TU Darmstadt)
Lukas Struppek gave an overview of several common attacks on deep learning systems and what impact they can have in practice

Prof. Dr. Josh Benaloh (Microsoft Research / University of Washington)
Prof. Dr Josh Benaloh showed how “end-to-end verifiability” can be used in elections to enable voters can confirm for themselves that their votes have been accurately counted - without having to trust any software, hardware, or personnel.

Prof. Dr. Christian Reuter (TU Darmstadt)
Prof. Dr. Christian Reuter presented the aims and challenges of the "Information Technology Peach Research" field, a discipline sitting at the cross road between computer science and pace & conflict research.

Oktober
Armin Harbrecht (Aramido)
Armin Harbrecht showed what can go wrong (and right) in communication between reporter and recipient of vulnerability disclosures based on his practical experience in both positions.

Prof. Dr. Nico Ebert (ZHAW)
Prof. Dr. Nico Ebert presented a talk titled "Understanding and Changing User Behavior in Security & Privacy: Applying the COM-B Model", in which he described the COM-B Model and the Behavior Wheel and how he employed it in a study on how to motivate TikTok users to engage with the app privacy settings.

Sebastian Roth (CISPA)
Sebastian Roth presented a talk titled "How to Deploy Security Headers Online (Consistently)" in which he gave an overview of his research, measuring the prevalence of security inconsistencies.

September
Prof. Dr. Oksana Kulyk (IT University of Copenhagen)
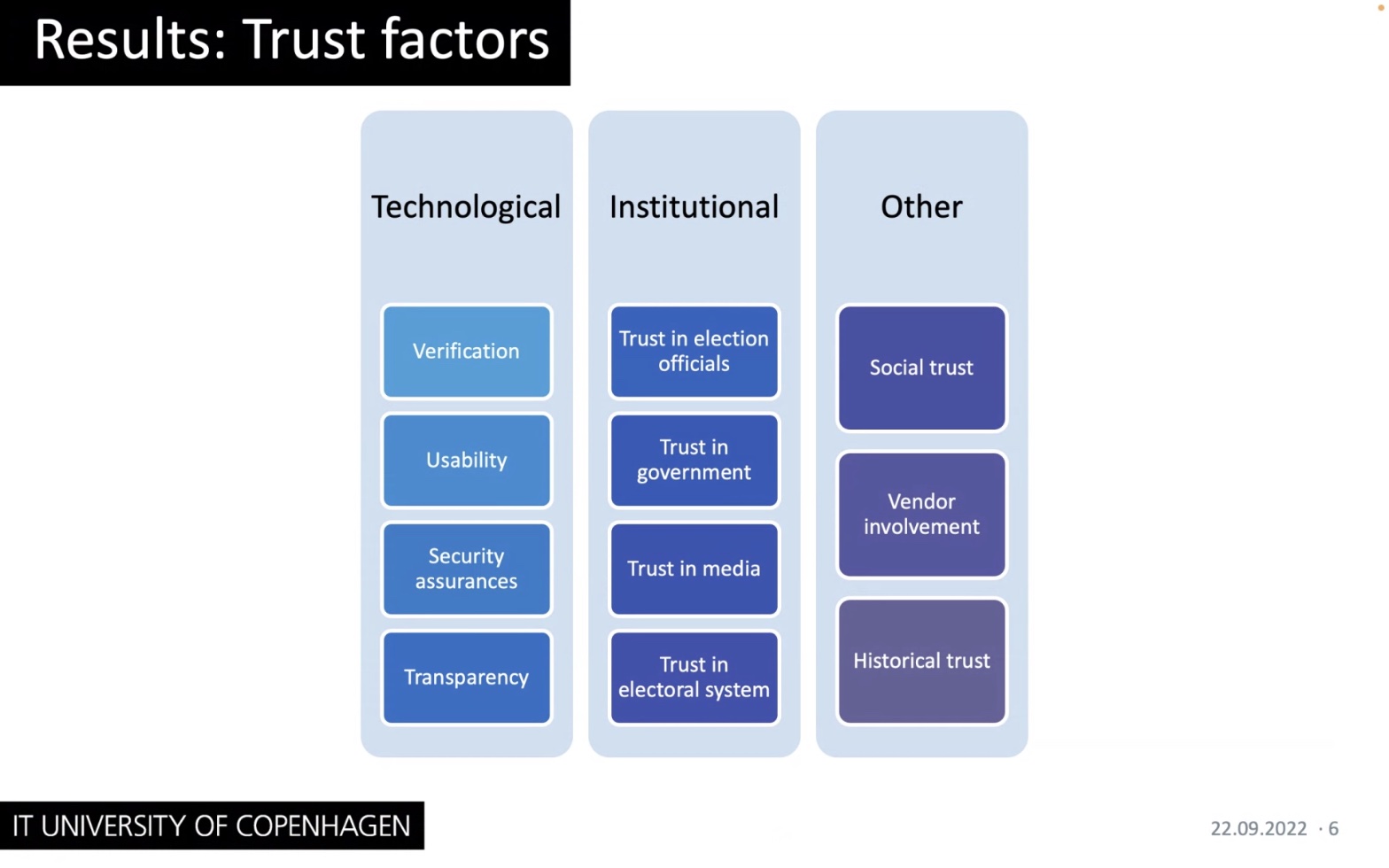
Prof. Dr. Oksana Kulyk presented a talk on perceived risks that voters have towards the use of election technologies, as well as identified 11 themes, representing factors, grouped into technological trust, institutional trust and others.
Prof. Dr. Vanessa Teaue ( Australian National University)
Prof. Dr. Vanessa Teague invited everyone to participate in a discussion about recent the European Union proposals to do client-side scanning of devices.

July
Prof. Dr. Oksana Kulyk (IT University of Copenhagen)
Prof. Dr. Oksana Kulyk presented a talk on the extension of a real world electronic voting system with a code-voting approach that increases the integrity of elections.

Benjamin Bachman (STRÖER)
Benjamin Backman presented a lecture on how to deal with information security in large enterprises.

June
Marius Krüger (DEMOCRACY - Deutschland)
Marius Krüger presented an overview of his app, DEMOCRACY, aimed at helping users discover howmuch their voting preferences align with actual votes in the German Bundestag.

Prof. Dr. Cristoph Krauß (Hochschule Darmstadt)
Prof. Dr. Krauß presented a talk on the current security and privacy of the electric vehicle charging architecture and advanced the proposal from a new model to protect against sleected threats.
May
Dr. David Dueñas-Cid (Gdansk University of Technology)
Dr. Dueñas-Cid presented a theoretical framework of trust and distrust and how they affect electronic voting using Netherlands 2006/2007 elections as example.

March
Prof. Dr. Simon Trang (Georg-August-Universität Göttingen)
Prof. Dr. Simon Trang presented his work "ITS.kompetent", an approach to identify, measure and develop task specific information security competencies of employees.

Dr. Ben Stock (CISPA)
Dr Ben Stock presented the evolution of Content Security Policies (CPS) over time and how website could leverage the to secure against three attack classes.

February
David Ruescas (Sequent)
David Ruescas presented us the story and technologies of Sequent, a Spanish start-up that offers end-to-end verifiable e-voting services.


